Development Processes
Description of processes and procedures related to the development of FMI products
This article is for IT and security professionals
Development process
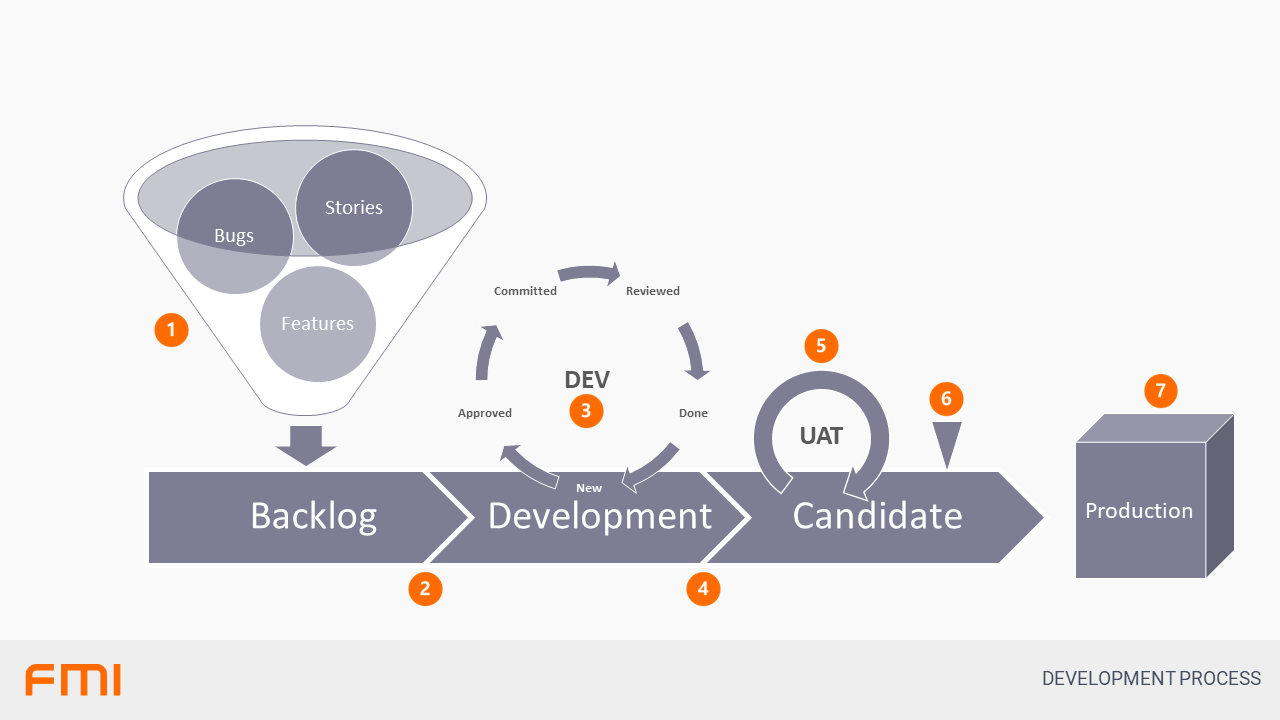
- The Product Owner is responsible for the management of all new work for the system, including Features, Bugs and User Stories. Working with the development team and customers to ensure the right work is done.
- A prioritised Backlog of work to be done is delivered to the development team at the beginning of each Release and each Sprint. Each Release is sub-divided into Sprints.
- The development team works on the items for the release using a formalised process of commitments and testing.
- All work in FMI is reviewed internally using a Pull Request system before it can be marked as Done.
- Testing is done during this review process using both automated and manual testing processes
- At the end of the development, the code is marked as Code Complete and a separate User Acceptance Test (UAT) environment is created.
- UAT testing occurs on this environment and Bugs are reported directly against UAT.
- Go/No-Go decision on each release, allowing the case where no release is better than a bad release.
- Final release to Production, using a gated continuous delivery pipeline so that the necessary steps are performed exactly as they were with UAT.
- Release notes are sent to clients highlighting features and bug fixes.
Key dates
- To UAT - first day after Code Complete.
- To Production - third Thursday of the month.
- Release Notes published - third Friday of the month.
Releases
Releases are scheduled once per month on the third Thursday of the month.
Releases typically contain 2x sprints worth of work. As sprints aren't aligned to months, occasionally there are additional sprints worth of work per release.
If additional time is available between code-complete and the release, this is used for additional testing.Risk-managed approach
Software development for FMI Works uses a risk-managed approach to development and maintain a risk register of all possible exploits and our fixes to those exploits.
This list is informed by client requirements, internal testing, automated vulnerability testing, manual penetration testing, the OWASP top 10 vulnerability lists for web and mobile, and the OWASP Application Security Verification Standard.
As a protection against vulnerabilities in third party software, every build of our software checks for known vulnerabilities in consumed libraries.
Hot fixes
Hot fixes are occasionally scheduled for Priority 1 (production down, no workaround) issues, or for time-sensitive issues (e.g., regulatory dates).
The entire automated release process is used whether a scheduled monthly release or a hot fix. Additional internal approvals are required to ensure fixes are as low-risk as possible and all departments are aware.
RCAs and Retrospectives are used to analyse all needs for hot-fixes and improve our internal processes.